Strengthening Cyber Defences: The Role of VAPT in Preventing Data Breaches

As the digital age progresses, so do cyber attackers and their tactics. Data breaches expose confidential and sensitive information, and they have become more prevalent than ever. A single breach can lead to huge losses – financial, legal, and reputational – and it can traumatise the victims involved. No organisation is exempt from the risks of a data breach, regardless of its size or industry.
Recent high-profile data breaches in Asia are stark reminders of the need for strong security measures. For example, Singapore’s largest healthcare institution, SingHealth, suffered Singapore’s worst cyber attack in 2018. Personal information of 1.5 million patients, including names, addresses, and medical records, was accessed by hackers, causing distress and loss of trust. Another breach occurred in 2018 when Hong Kong-based airline Cathay Pacific Airways was attacked, affecting 9.4 million passengers. Personal data, including passport details and credit card information, was exposed.
Cyber attackers continue to terrorise the region in the present day: Singapore luxury resort Marina Bay Sands was affected by a data breach that accessed the personal data of 665,000 lifestyle members in November this year.
It’s more critical than ever for businesses to safeguard sensitive information and defend against cyber threats, which requires proactive steps. Vulnerability Assessment and Penetration Testing (VAPT) services are an effective way to mitigate the risk of data breaches.
How do data breaches happen?
A data breach occurs when unauthorised parties access, steal, or compromise sensitive information such as customer data, financial records, intellectual property, or trade secrets. Data breaches can have devastating consequences for businesses, from regulatory fines, loss of revenue and legal liability, to reputational damage and loss of customer trust.
Types of data breaches
Data breaches can be classified into two types – intentional and accidental.
Intentional data breaches are perpetrated by malicious actors who secure access to systems to steal or destroy data. The most common causes of intentional data breaches include phishing attacks, malware or ransomware, malicious insiders, social engineering, and denial of service attacks.
Accidental data breaches happen when an organisation fails to secure its systems properly, or when employees unintentionally mishandle sensitive information. The most common causes of accidental data breaches are weak passwords, lack of encryption on sensitive files or networks, lack of employee training on security protocols and procedures, and inadequate access controls.
Here is a quick look at the most common types of data breaches:
- Ransomware is a type of malware that encrypts the victim’s data and demands a ransom for its decryption. Ransomware attacks have become more prevalent and sophisticated in recent years, due to the availability of ransomware-as-a-service (RaaS) platforms and cryptocurrencies that enable anonymous payments. Ransomware attacks can disrupt business operations, compromise sensitive data, and extort large sums of money from victims.
- Phishing is a type of social engineering attack that uses fraudulent emails or websites to trick users into revealing their personal or financial information or clicking on malicious links or attachments. Phishing attacks can lead to identity theft, account takeover, malware infection, and data leakage. Phishing attacks increased significantly during the COVID-19 pandemic, as cybercriminals exploited the fear and uncertainty of the situation.
- Denial of service (DoS) attacks are a type of cyberattack that attempts to prevent legitimate users from accessing a system, network, or application. DoS attacks can be used to disrupt business operations and extort money from victims. The most common types of DoS attacks are flooding attacks, which involve sending large amounts of malicious traffic to overwhelm the target’s resources. Other types of DoS attacks include application-level, protocol-level, and distributed denial of service (DDoS) attacks. DDoS attacks are particularly dangerous, as they can involve thousands or even millions of compromised devices (botnets) to launch a coordinated attack.
- Insider threats are one of the most concerning types of data breaches, as they involve trusted individuals within the organisation who have access to sensitive data and systems. Insider threats can be malicious, such as disgruntled employees or contractors intentionally causing harm, or unintentional, such as employees falling victim to phishing attacks or accidentally leaking confidential information. Organisations need to have strict security policies and procedures in place to detect and prevent insider threats.
Take proactive security measures.
Cybersecurity incidents are happening more often and becoming more complex, which means that businesses need to be taking proactive security measures. Waiting for a data breach to happen before taking action can result in catastrophic consequences. IBM says that for 83% of companies, it’s not if a data breach will happen, but when.
Proactive steps to protect data and networks from cyber threats include implementing security best practices such as using strong passwords, patching systems regularly, encrypting sensitive data, and regularly monitoring for suspicious activity. Further, companies should educate their staff on cybersecurity awareness and have a plan in place to respond quickly to security incidents. Cybersecurity is a shared responsibility, and everyone should take steps to protect their digital assets.
Understanding Vulnerability Assessment (VA) and Penetration Testing (PT)
Vulnerability assessments involve systematically scanning and analysing IT infrastructure to identify potential weaknesses and security flaws. It is a proactive approach that allows businesses to discover vulnerabilities before they can be exploited.
Recent cybersecurity incidents in Asia have highlighted the importance of vulnerability assessments. For example, in 2021, Mercari, a major e-commerce platform in Asia, experienced a data breach due to unpatched vulnerabilities in their web application. A VAPT assessment would have identified and patched these vulnerabilities, which would have prevented the breach and the subsequent damage to the company’s reputation and customer trust.
What are VAPT services and how do they work?
Vulnerability Assessment and Penetration Testing (VAPT) is a proactive set of techniques used to identify, assess, and fix network or software vulnerabilities, and ensure the protection of a company’s critical data.
VAPT services help organisations to:
- Detect and prioritise security weaknesses in their IT infrastructure, such as servers, networks, databases, web applications, mobile applications, cloud services, etc.
- Simulate real-world attack scenarios and measure their potential damage and likelihood.
- Validate the effectiveness of existing security controls and policies.
- Provide actionable recommendations for remediation and improvement.
- Comply with industry standards and regulations, such as PCI DSS, ISO 27001, HIPAA, GDPR, etc.
VAPT services can be performed by internal or external experts, depending on the organisation’s needs and resources. However, it is important to choose a reputable and qualified VAPT service provider that has the necessary skills, experience, tools, and methodologies to conduct a thorough and reliable security assessment.
Some of the benefits of outsourcing VAPT services to a professional provider are:
- Access to specialised knowledge and expertise that may not be available in-house.
- Reduced costs and time compared to hiring and training internal staff.
- Independent evaluation of the organisation’s security posture.
- Continuous monitoring and support throughout the VAPT process.
Proactive cybersecurity is an investment, not an expense.
Some businesses may see VAPT services as an unnecessary expense. However, they should view it as an investment in protecting valuable company assets. The costs of a data breach far outweigh the expenses of implementing VAPT services. Businesses must understand that preventing data breaches is more cost-effective than dealing with the aftermath.
IBM’s 2023 Cost of a Data Breach report indicates that the global average cost of a data breach globally in 2023 was US $4.45 million, and the average time to identify and contain a breach is 277 days. The report also found that the average cost of a data breach in the ASEAN region increased 6% from 2022 to US $ 3.05 million.
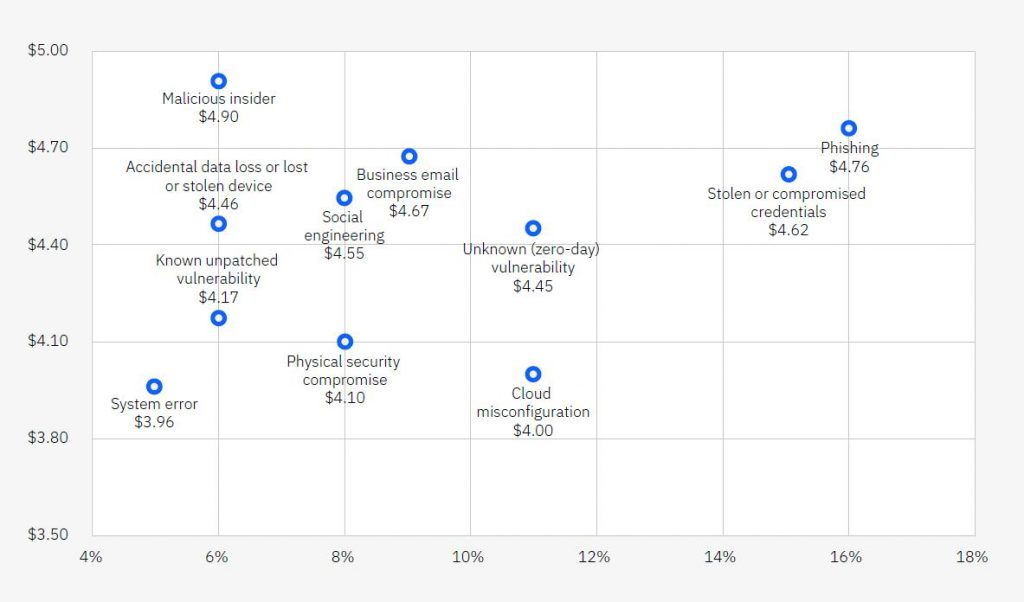
Figure 1 Cost and frequency of a data breach by initial attack vector, measured in USD millions. Source: Cost of a Data Breach Report 2023, IBM
VAPT services help businesses avoid financial losses, legal fees, and reputational damage from data breaches. They also help ensure compliance with regulations and avoid penalties.
In addition to identifying vulnerabilities and providing recommendations, VAPT services offer businesses an opportunity to enhance their security. Regularly conducting VAPT assessments helps organisations identify trends and patterns in security vulnerabilities, which allows them to make informed decisions on strengthening cybersecurity defenses. This proactive approach helps prevent future data breaches and saves businesses from potential financial losses.
Conclusion
In conclusion, data breaches are a real and significant threat in the digital age. VAPT services play an essential role in helping businesses protect themselves from potential attacks and mitigate the risks of a breach. Investing in VAPT services and other security measures will help businesses safeguard sensitive information, reduce financial losses, preserve customer trust, and ensure the security of their operations.
It is also important for businesses to stay up to date on the latest cybersecurity trends and threats. With proactive action, they can remain one step ahead of cybercriminals and protect their critical data and customer information from any potential harm. The key is to take effective measures now in order to prepare for any future security incidents. With the right strategies and tools in place,businesses can stay ahead of cybercriminals and protect themselves from any malicious attacks.



















