Securing Your Network with a Dispersed Workforce

In a report published in 2019, the Cyber Security Agency (CSA) highlighted 5 major security threats that predominated Singapore’s cyber landscape. Malware, short for malicious software, comprised one of these threats. To combat them, business owners typically secure their business with single- or multi-layer security appliances.
However, as businesses have now dispersed from workplaces into individual homes, there are risks that could expose vulnerabilities in business cybersecurity. Businesses have typically considered workplace cybersecurity from the perspective of depth, layering network security solutions on top of each other to strengthen the whole.

Is your business secure with employees working from home?
In light of how COVID-19 has dispersed the global workforce from the traditional office into business continuity sites and the home, we believe that it is necessary for businesses to start thinking about cybersecurity from a horizontal perspective that spans all of these new working environments. Until a return to full normalcy, we foresee most workers continuing to shift between the 2 states of working from home and resuming Business as Usual.
With this new status quo in mind, we want to highlight 3 areas of cybersecurity that business owners should take note of in order to be prepared for well-secured, uninterrupted operations going ahead. These are:
- 1. Asset-Level Security
- 2. Site-Level Security
- 3. Network-Level Security

Asset-Level Security
Phishing with malware and computer viruses are the most common cybersecurity threats that can compromise your business’ IT assets. Yet, as discovered in IMDA’s 2019 survey on Enterprise Infocomm Usage, only 42% of businesses had some form of cybersecurity measure in place, down from 52% in 2017. Even for micro-sized businesses with budget constraints, antivirus software is a default must-have to protect your equipment.
Aside from computer devices, another commonly overlooked IT asset susceptible to security breaches is the router. Now that many of us are working from home, the security of routers at home are as important as those at the workplace.

When was the last time you changed your password?
However, many might shy away from the question, “when was the last time you changed the password of your home router?” As reported in 2018, the CSA found that more than 60% of respondents in its Public Awareness survey generally
do not change their passwords regularly, or do so only when they are prompted. They also recommend using at least 12 random characters to create a reasonable length password to mitigate the risks involved when passwords are not regularly updated.
As best practice, we recommend protecting your IT assets at home or at the workplace with frequent changes to device and router passwords, install antivirus and anti-malware software, and by sending staff for anti-phishing training.

Site-Level Security
Even after changing the password of your WiFi router, your devices can still be at risk if your family members’ or teammates’ devices have already been infected with malware. Malware can potentially infect your own devices when you connect to common home devices such as home network access storage (NAS) devices.
Most WiFi routers come with a firewall, but if you do not know how to set it up or if the settings are not customised to your company’s security guidelines, these security features could be left in its default setting and remain ineffective. Furthermore, not all firewalls are built the same; consumer-grade home WiFi routers are usually more susceptible to cyber breaches, whereas enterprise-grade security appliances can better mitigate potential risks. Their firewall settings would also be more stringent and are more likely universally configured and managed.
While this appears to be unnecessary for the home, if you work with critical and sensitive business data, it might be a meaningful investment to make as we have to shuffle between working from the office and home.
We also highly recommend having a separate wireless network name (SSID) for your organisation in your temporary business continuity site like co-working spaces, or even at home. This would allow you to separate your work data from other WiFi networks.

For the best security, have a separate wireless network SSID
To achieve this, you can use a WiFi enabled security appliance (with firewall) connected to the LAN port at your temporary site or connected to the home router.

Network-Level Security
Many SMEs own file servers that their employees access on a daily basis, but this is not usually designed to be accessed from outside the office, especially in a situation where most of the staff are required to work from home. Setting up a Virtual Private Network (VPN) would enable you to access your sensitive data over an encrypted tunnel, but this tends to become more complex when we need to have dual internet links at the HQ, multiple branches, temporary sites, and home offices.
Given this circumstance, we recommend business owners and IT heads to invest in all-in-one routers that come with WiFi, Firewall, VPN capabilities to be ready for dynamic situations.
Network-Level Security
With a dispersed workforce, the dynamics of securing the network is more complex and when it comes to protecting mission-critical business data, there is a low margin for error. There’s a need to adopt a horizontal perspective on top of a layered one so that our organisations are able to react to rapidly evolving security needs.
One of the security solutions that we’d like to recommend is Cisco Meraki’s Z3 series, which is a cost effective WiFi gateway that helps you to achieve the segregation of WiFi SSID at multiple sites.
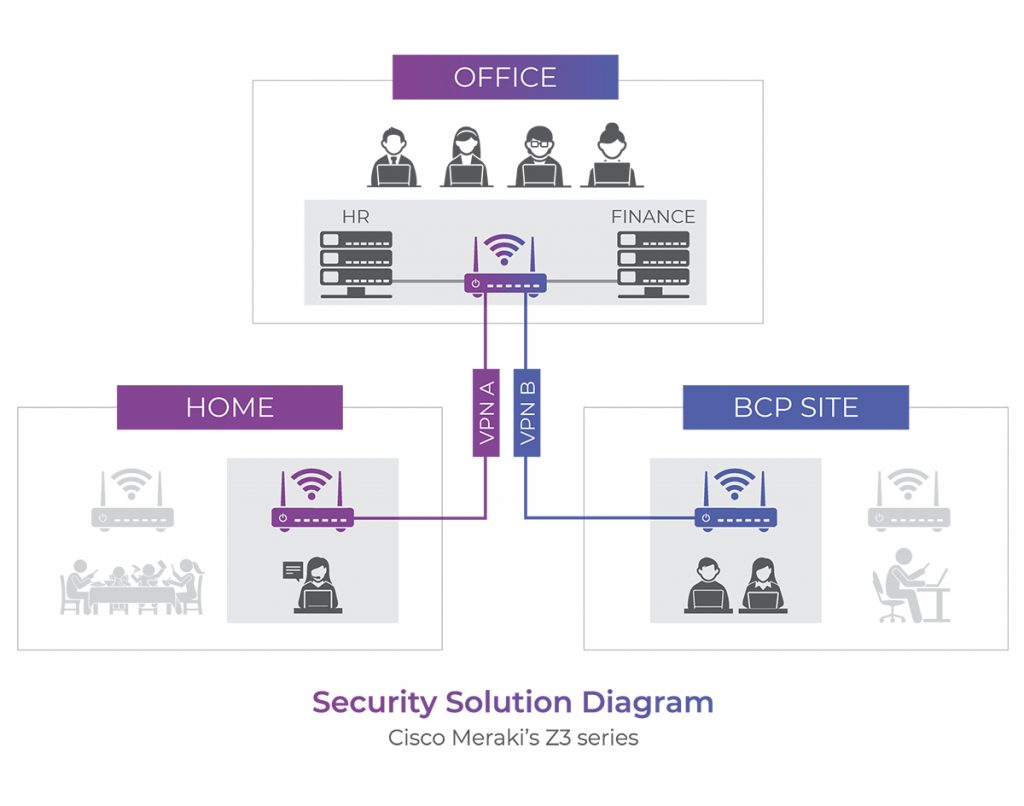
Investing in dual firewalls in your home such as your existing home WiFi router and a Cisco Meraki device helps to create layered protection against online intruders. Embedded with a stateful Layer 3 and Layer 7 firewall protection, intruders would be greatly challenged in their attempts to access your precious data and systems.
For protection against insidious malware, there is the Cisco Meraki’s MX64W, a device that can automatically block sites suspected or known for spreading malware.
These Cisco Meraki devices are deployed locally in BCP sites or home offices, but have the ability to connect automatically and seamlessly to the business HQ based on the SD-WAN powered VPN function, allowing you easy access to the file servers over an encrypted tunnel.

The Cisco Meraki MX64W
This access can be separated according to different departments and file servers, such as one VPN for Finance and another for Human Resources. The SD-WAN feature allows complex deployment environments where important file servers are replicated to redundancy sites.
Taking on this horizontally and vertically layered approach to cybersecurity consequently enables your business to easily adapt and address new needs to cope with an increasingly distributed workforce.
Authorised as a Managed Service Provider with the Cisco Meraki platform since 2018, MyRepublic has been managing thousands of network nodes securely for our customers, many of whom also subscribe to a resilient combination encompassing both fibre broadband and LTE network connectivity.Read more about how we conduct our Managed Services here, or get in touch with our team.



















